[New Exam]Braindump2go 800-150 VCE Dumps Free Share[Q1-Q20]
2025 New Braindump2go Cisco 800-150 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 800-150 Exam Questions!
Supporting Cisco Devices for Field Technicians (FLDTEC 800-150) is a 120-minute exam associated with the Cisco Certified Technician Certification. This exam tests a candidate’s knowledge and skills related to on-site replacement of Cisco technologies across routing, switching, data
center, UCS, and collaboration platforms. This includes hardware identification, cabling, configuration backup and restoration, and software upgrades/downgrades. The Cisco Certified Technician course helps candidates prepare for this exam.
More general guidelines for the content likely to be included on the exam: https://learningcontent.cisco.com/documents/marketing/exam-topics/800-150_FLDTEC_v1.0.pdf
Question: 1
[Cisco Equipment and Related Hardware]
What is the primary role of a switch in a local area network?
A. to route data packets between different networks
B. to encrypt data transmissions for security
C. to divide the network into separate collision domains
D. to provide wireless connectivity to LAN devices
Answer
Explanation:
In a local area network (LAN), the primary function of a switch is to operate at Layer 2 (Data Link Layer) of the OSI model. Switches use MAC addresses to forward frames to the appropriate destination ports. This targeted forwarding mechanism divides the network into separate collision domains for each switch port. By isolating collision domains, switches significantly reduce the chance of collisions, enhancing the performance and efficiency of the network.
Unlike hubs, which forward all traffic to all ports (thus creating a single collision domain), switches intelligently forward only the necessary traffic to the correct port. This capability allows multiple simultaneous conversations on different switch ports without interference.
Routers, which operate at Layer 3 (Network Layer), are used to route packets between different networks, not within the same LAN. Wireless connectivity is provided by wireless access points (WAPs), not switches. Encryption is typically handled by security protocols or devices such as firewalls and not by switches directly.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 2
[Cisco Equipment and Related Hardware]
Which Layer 2 technology extends to access layer devices, allowing individual switch ports to be
assigned for network and traffic management in an enterprise network?
A. BGP
B. VLANs
C. OSPF
D. MPLS
Answer: B
Explanation:
In an enterprise network, Virtual Local Area Networks (VLANs) are the key Layer 2 technology used to logically segment a network into multiple broadcast domains. VLANs allow network administrators to assign individual switch ports to specific VLANs, enabling effective network segmentation and traffic management.
This configuration extends to access layer devices, such as switches where end-user devices connect. By isolating traffic into VLANs, administrators can improve network performance, enhance security by separating sensitive departments (such as finance and HR), and simplify network management.
Unlike routing protocols such as BGP and OSPF, which operate at Layer 3, or MPLS, which is a Layer
2.5 forwarding technology used primarily in service provider networks, VLANs are explicitly designed for Layer 2 segmentation within LAN environments.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 3
DRAG DROP
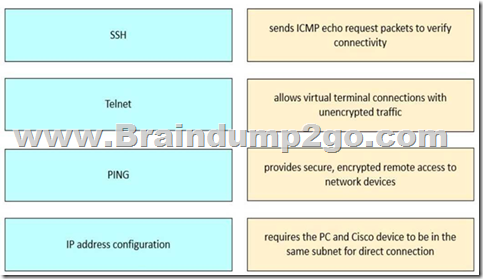
[Device Configuration and Verification]
Drag and drop the network connectivity and management tools used to ensure connectivity from the left onto the description on the right.
Answer:
PING → Sends ICMP echo request packets to verify connectivity Telnet → Allows virtual terminal connections with unencrypted traffic SSH → Provides secure, encrypted remote access to network devices
IP address configuration → Requires the PC and Cisco device to be in the same subnet for direct connection
These tools and their functions are covered under “Device Configuration and Verification” in the FLDTEC course:
PING: Utilized to test basic network connectivity using ICMP echo request/reply messages. It confirms whether a device is reachable and measures the round-trip time.
Telnet: A protocol that allows for remote device access but transmits data in plaintext, which makes it insecure. It’s typically disabled by default on modern Cisco devices due to security concerns.
SSH (Secure Shell): Replaces Telnet as the preferred method for secure CLI access. It encrypts the session, protecting sensitive information such as login credentials.
IP Address Configuration: For direct device access via the same local network, both the PC and the Cisco device must be in the same subnet. This allows the use of tools like browser-based GUIs or terminal emulators when connecting directly.
Question: 4
[Troubleshooting Methodologies]
Which scenario would result in a speed mismatch when configuring Ethernet devices with different speed settings?
A. One end is manually set to 1 Gbps, and the other end is manually set to 100 Mbps
B. Both ends are manually set to the same speed
C. One end is manually set to 100 Mbps, and the other end is set to auto-negotiation
D. Both ends are set to auto-negotiation and fail, reverting to their lowest speeds
Answer: A
Explanation:
A speed mismatch occurs when two connected Ethernet devices are configured to operate at different speeds. In scenario A, one device is manually set to 1 Gbps, while the other is set to 100 Mbps. Since both ends are hard-coded to different speeds, they cannot successfully negotiate a common speed, leading to a mismatch and resulting in a failed or unstable link.
In contrast, scenario B, where both ends are manually set to the same speed, ensures compatibility and stable communication. Scenario C can lead to a duplex mismatch rather than a speed mismatch; the auto-negotiating end may default to half-duplex if it cannot determine the duplex setting of the manually configured end. Scenario D is less common; if auto-negotiation fails, devices may revert to their lowest common speed, but this typically results in reduced performance rather than a complete mismatch.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Troubleshooting Methodologies
Question: 5
[Cisco IOS Software Basics]
Which layer of the OSI model provides error detection and defines how access to the media is controlled?
A. Presentation layer
B. Physical layer
C. Network layer
D. Data link layer
Answer: D
Explanation:
The Data Link Layer (Layer 2) of the OSI model is responsible for node-to-node data transfer and plays a crucial role in error detection and media access control. It ensures that data frames are transmitted to the correct device on a local network segment.
This layer is divided into two sublayers:
Logical Link Control (LLC): Manages frame synchronization, flow control, and error checking. Media Access Control (MAC): Controls how devices on the network gain access to the medium and permission to transmit data.
Together, these sublayers ensure reliable data transmission by detecting and possibly correcting errors that may occur in the Physical Layer. They also manage how devices share the transmission medium, preventing collisions and ensuring orderly communication.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco IOS Software Basics
Question: 6
DRAG DROP
[Cisco Equipment and Related Hardware]
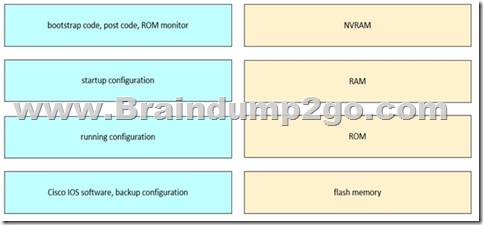
Refer to the exhibit. Drag and drop the functions from the left onto the corresponding internal memory components on the right.
Answer:
Explanation:
NVRAM → Startup configuration RAM → Running configuration
ROM → Bootstrap code, POST code, ROM monitor
Flash memory → Cisco IOS software, backup configuration
Each memory type in a Cisco device serves a specific function in the boot process and runtime operation. NVRAM retains configuration across reboots, RAM is volatile and holds active configs, ROM handles initial boot tasks, and flash stores the operating system.
This content is covered thoroughly in “Cisco Equipment and Related Hardware” in the FLDTEC curriculum. Here’s the breakdown:
ROM (Read-Only Memory)
Stores bootstrap code, POST (Power-On Self-Test), and ROM Monitor.
These are essential for the device’s initial power-on operations and recovery modes. NVRAM (Non-Volatile RAM)
Holds the startup configuration file, which is loaded during the boot process. Content remains intact after a reboot or power cycle.
RAM (Random Access Memory)
Stores the running configuration and current operational state of the router or switch. Also used for routing tables, ARP cache, and packet buffers.
Data is lost when the device is powered off or rebooted. Flash Memory
Contains the Cisco IOS image, system files, and can store backup configurations. It is a non-volatile storage, so it retains data after reboots.
Question: 7
[Cisco Equipment and Related Hardware]
Which two devices are most commonly used in a WAN environment? (Choose two.)
A. Hubs
B. Optical fiber converters
C. Modems
D. Network interface cards
E. Wireless access points
Answer: BC
Explanation:
In the context of Wide Area Networks (WANs), the key objective is to connect geographically separated networks using service provider infrastructure. The FLDTEC course emphasizes that WAN environments typically involve devices that can handle different physical transmission mediums and protocols.
Modems:
Modulate and demodulate analog signals to digital signals.
Used in WAN environments to connect over analog lines like DSL or leased lines. Essential for interfacing between digital routers and analog telephone networks. Optical Fiber Converters:
Also known as media converters, they are used to convert electrical signals to optical signals (and vice versa) for fiber transmission.
Common in WAN scenarios where long-distance high-speed transmission over fiber is required. Incorrect Options:
A . Hubs: Obsolete Layer 1 devices used in LANs, not suitable for WANs.
D . Network Interface Cards (NICs): Used in end devices for LAN connectivity.
E . Wireless Access Points: Typically used in WLANs within local premises, not WAN infrastructure. This aligns with Cisco’s WAN architecture fundamentals as highlighted in FLDTEC under “Cisco Equipment and Related Hardware.”
Question: 8
[Cisco IOS Software Basics]
What is the purpose of a subnet mask?
A. Distinguishes the network and host segments
B. Provides encryption for network traffic
C. Determines the next-hop router
D. Aids in route prioritization
Answer: A
Explanation:
A subnet mask is a 32-bit number used in IP networking to divide an IP address into network and host portions. This division is crucial for routing traffic within and between networks. The subnet mask works in tandem with the IP address to identify which part of the address refers to the network and which part refers to the host. This distinction allows for efficient IP address allocation and routing.
For example, in the IP address 192.168.1.10 with a subnet mask of 255.255.255.0, the first three octets (192.168.1) represent the network portion, while the last octet (10) identifies the specific host within that network.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco IOS Software Basics
Question: 9
DRAG DROP
[Device Configuration and Verification]
Drag and drop the descriptions from the left onto the corresponding IPv4 addressing modes on the right.
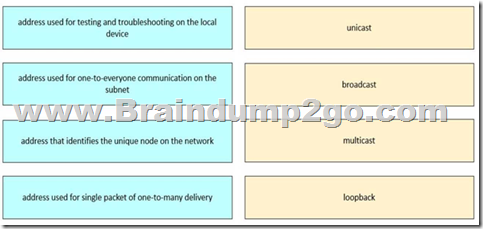
Answer:
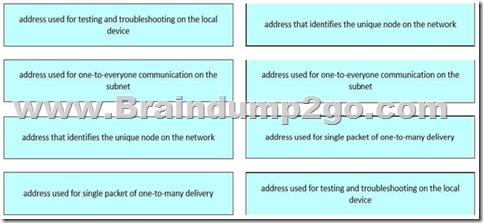
Explanation:
This content is aligned with IPv4 Addressing Fundamentals, detailed in the FLDTEC course under Device Configuration and Verification:
Unicast: A unicast address uniquely identifies a single host on a network. This is the most common address type used for standard communication between two devices.
Broadcast: Broadcast addresses (e.g., 255.255.255.255 or subnet-specific broadcast) send traffic to all hosts in the network segment. Used for ARP requests and DHCP discovery.
Multicast: Used to deliver a packet to a group of hosts interested in the data, without flooding the network like a broadcast. Multicast uses addresses from the range 224.0.0.0 to 239.255.255.255. Loopback: The loopback address (127.0.0.1) is reserved for local testing, ensuring that the TCP/IP stack is working properly without needing to access the network.
Question: 10
[Cisco Equipment and Related Hardware]
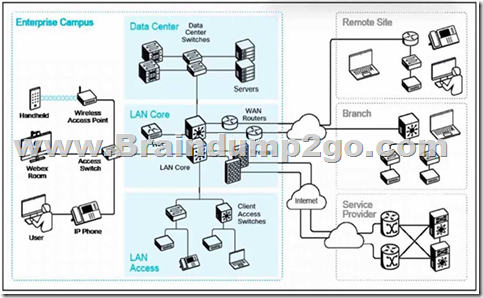
Refer to the exhibit. What are two ways remote sites or branches connect to the enterprise campus network? (Choose two.)
A. Access layer switches
B. WAN links
C. IPsec VPN tunnels
D. Ad hoc Wi-Fi network
E. LAN core switches
Answer: B, C
Explanation:
In enterprise networking, remote sites or branch offices connect to the central campus network using:
WAN Links: These are dedicated communication paths that connect geographically dispersed networks. WAN links can be leased lines, MPLS circuits, or other forms of long-distance connectivity that facilitate reliable data transmission between remote sites and the main campus.
IPsec VPN Tunnels: Internet Protocol Security (IPsec) VPNs provide secure, encrypted tunnels over the public internet, allowing remote sites to connect to the enterprise network securely. This method is cost-effective and widely used for connecting branch offices to the central network infrastructure. Access layer switches (Option A) and LAN core switches (Option E) are components within a local network and do not facilitate remote connectivity. Ad hoc Wi-Fi networks (Option D) are temporary and lack the security and reliability required for enterprise-level remote connections.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 11
[Cisco Equipment and Related Hardware]
When should a crossover UTP cable be used instead of a straight-through cable when connecting network devices?
A. To connect electrically like devices
B. To connect a PC to a wireless access point
C. To connect a switch to a router
D. To connect electrically unlike devices
Answer: A
Explanation:
A crossover UTP (Unshielded Twisted Pair) cable is used to connect two similar devices directly. This includes:
Switch to switch Router to router PC to PC
The crossover cable reverses the transmit and receive pairs, allowing for proper communication between like devices without the need for an intermediary device.
Conversely, a straight-through cable is used to connect dissimilar devices, such as: PC to switch
Router to switch PC to router
This cable maintains the same wiring on both ends, suitable for connecting different types of devices. Therefore, when connecting electrically like devices, a crossover cable is appropriate.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 12
[Cisco IOS Software Basics]
How many bits are borrowed from the default host portion of the address to create subnets in a Class B network with a subnet mask 255.255.255.0?
A. 3 bits
B. 5 bits
C. 3 bits
D. 8 bits
Answer: D
Explanation:
In a Class B network, the default subnet mask is 255.255.0.0, which allocates: 16 bits for the network portion
16 bits for the host portion
When the subnet mask is changed to 255.255.255.0, it becomes: 24 bits for the network portion
8 bits for the host portion
This indicates that 8 bits have been borrowed from the host portion to create additional subnets. Borrowing bits allows for the division of the original network into smaller sub-networks, enhancing organization and security within the network.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco IOS Software Basics
Question: 13
[Cisco Equipment and Related Hardware] What is the function of an access layer device?
A. Provides high-speed data transport between buildings or different parts of the campus
B. Serves as the entry point for end-user devices to connect to the network
C. Provides secure external access to internal network components
D. Connects remote offices to the main corporate network
Answer: B
Explanation:
In the hierarchical network design model, the access layer is the first layer and serves as the entry point for end-user devices to connect to the network. This layer connects user devices such as PCs, IP phones, wireless access points, printers, and scanners to the network. It facilitates the initial connection between end-user devices and the network infrastructure. The access layer also enforces security policies and provides services such as VLAN membership, port security, and Quality of Service (QoS).
Options A, C, and D refer to functions typically associated with the core or distribution layers, or with WAN connectivity, rather than the access layer.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 14
[Wireless Device Support]
Which term describes the physical range of radio frequency coverage provided by an access point in a wireless topology?
A. Service Set Identifier (SSID)
B. Basic Service Area (BSA)
C. Wireless LAN (WLAN)
D. Wireless LAN Controller (WLC)
Answer: B
Explanation:
In wireless networking, the Basic Service Area (BSA) refers to the physical area of radio frequency coverage provided by an access point (AP) in a Basic Service Set (BSS). The BSA defines the coverage area where wireless clients can connect to the network through the AP. The size and shape of a BSA depend on various factors, including the AP’s transmit power, antenna type, and physical environment.
Option A, the Service Set Identifier (SSID), is the network name broadcast by the AP. Option C, Wireless LAN (WLAN), refers to the overall wireless network. Option D, Wireless LAN Controller (WLC), is a device that manages multiple APs in a network.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Wireless Device Support
Question: 15
[Device Configuration and Verification]
Which two configuration parameters are most critical to ensure optimal performance when configuring a network port for a newly installed IP phone in an enterprise environment? (Choose two.)
A. VLAN assignment
B. Link aggregation
C. Spanning Tree Protocol
D. Power over Ethernet
E. QoS classification
Answer: A, D
Explanation:
When configuring a network port for a newly installed IP phone, two critical parameters to ensure optimal performance are:
VLAN Assignment: Assigning the correct VLANs is essential for segregating voice and data traffic. Typically, a separate voice VLAN is configured to prioritize voice traffic and enhance security.
Power over Ethernet (PoE): PoE allows the switch to supply power to the IP phone over the same Ethernet cable used for data transmission. This eliminates the need for separate power supplies and simplifies installation.
While QoS classification (Option E) is important for prioritizing voice traffic, it is typically configured at a broader network level. Link aggregation (Option B) and Spanning Tree Protocol (Option C) are more relevant to network redundancy and loop prevention, respectively, and are not directly critical for the initial configuration of an IP phone port.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Device Configuration and Verification
Question: 16
Which deployment scenarios are Cisco 8000 Series routers primarily designed for?
A. remote branch offices and retail locations
B. service provider and web-scale networks
C. small business and home office networks
D. campus LAN access and distribution layers
Answer: B
Explanation:
Cisco 8000 Series routers are primarily designed for service provider and web-scale networks, offering high-performance routing capabilities to handle large-scale, high-bandwidth environments typically found in service provider infrastructures and data centers.
Question: 17
DRAG DROP
[Cisco IOS Software Basics]
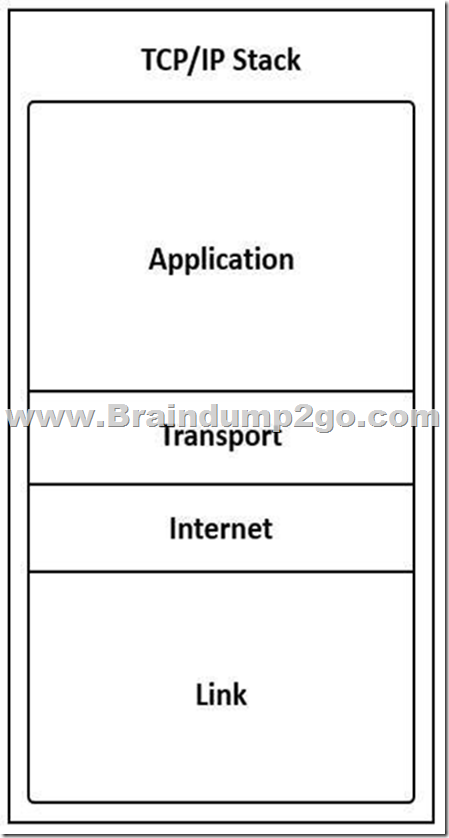
Refer to the exhibit. Drag and drop the steps in the TCP/IP encapsulation process from the left onto the corresponding layer on the right.
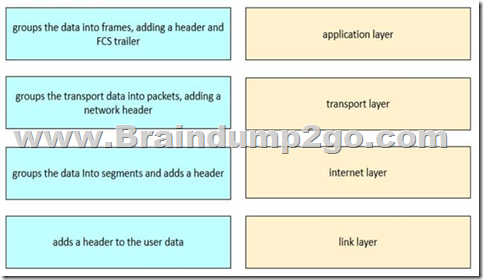
Answer:
Explanation:
The FLDTEC training describes the TCP/IP encapsulation as a step-by-step process where data is
passed down through the layers of the TCP/IP model:
Application Layer: User data is created (email, file, request) and the application layer adds the application header, creating a data payload.
Transport Layer: The data is segmented. Each segment receives a transport-layer header (TCP/UDP), enabling proper sequencing and error handling at the destination.
Internet Layer: Segments are encapsulated into packets (IP datagrams), with an IP header added to facilitate routing between networks.
Link Layer: Finally, packets are framed with Layer 2 headers and trailers (including the Frame Check Sequence for error detection), creating a frame ready to be transmitted on the physical medium. This layered encapsulation ensures interoperability and troubleshooting clarity, which is why it is emphasized in FLDTEC’s IOS Software Basics module.
Question: 18
[Cisco Equipment and Related Hardware]
Which Cisco switch series is designed to handle the combined responsibilities of core and distribution layers in a converged architecture?
A. Meraki MS400 Series
B. Catalyst 6500 E-Series
C. Catalyst 1300 Series
D. Catalyst 9000 Series
Answer: D
Explanation:
The Cisco Catalyst 9000 Series is engineered to address the evolving needs of modern enterprise networks by integrating the functionalities of both the core and distribution layers into a unified, converged architecture. This series offers advanced capabilities such as high-speed data forwarding, enhanced security features, and support for automation and programmability, making it suitable for scalable and efficient network designs.
The Catalyst 9000 Series includes models like the Catalyst 9500 and 9600, which are optimized for core and distribution roles, providing high throughput and reliability. These switches support advanced features like Software-Defined Access (SD-Access) and are designed to meet the demands of cloud-scale and security-focused environments.Wikipedia+2Cisco+2Cisco+2
In contrast, the Meraki MS400 Series (Option A) is tailored for cloud-managed aggregation and lacks the comprehensive feature set required for core functionalities. The Catalyst 6500 E-Series (Option B), while historically significant, is considered a legacy platform and may not support the latest advancements in network convergence. The Catalyst 1300 Series (Option C) is designed for small to medium-sized businesses and is not intended for core or distribution layer deployments.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Cisco Equipment and Related Hardware
Question: 19
DRAG DROP
[Device Configuration and Verification]
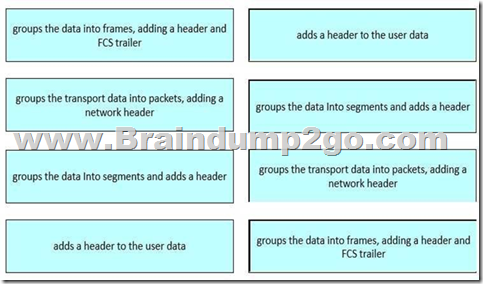
Drag and drop the configuration tasks for restoring software from the left onto the corresponding commands on the right.
Answer:
Explanation:
These command associations are part of Cisco IOS essentials taught in FLDTEC’s “Device Configuration and Verification” topic. Here’s how each command functions:
show running-config
Displays the active configuration stored in RAM.
This command is used to verify the current settings on a Cisco device.
copy running-config startup-config
Saves the current running configuration to NVRAM, ensuring the configuration persists after a reboot.
This is critical after making changes to device settings. copy tftp: running-config
Loads a configuration from a TFTP server and applies it to the current running configuration. Often used during remote device setup or restoration.
copy usbflash0:backup.cfg running-config
Restores a saved configuration file from a USB drive.
Useful in field operations where physical backup media is used during maintenance.
These tasks are routine for field technicians performing configuration backups, restorations, and diagnostics in Cisco environments.
Question: 20
[Maintenance and RMA Procedures]
Which command is used to download a copied configuration file from a TFTP server to merge it with the running configuration of a replacement Cisco device?
A. load tftp: running-config
B. copy tftp: startup-config
C. copy tftp: running-config
D. merge tftp: running-config
Answer: C
Explanation:
The command copy tftp: running-config is used to retrieve a configuration file from a TFTP server and merge it with the current running configuration of a Cisco device. This operation is additive, meaning it integrates the new configuration commands into the existing running configuration without removing any pre-existing commands unless explicitly overridden.
This method is particularly useful when restoring configurations to a replacement device, as it allows for the seamless integration of necessary settings without disrupting the current operational state.
In contrast, using copy tftp: startup-config would overwrite the startup configuration file, which could lead to unintended consequences upon the next device reload. The options load tftp: running-config and merge tftp: running-config are not valid Cisco IOS commands.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Maintenance and RMA ProceduresCisco
Question: 21
[Maintenance and RMA Procedures]
What is the primary purpose of backing up the endpoint configuration prior to replacing the device?
A. To troubleshoot network connectivity issues
B. To update the firmware of the device
C. To generate a performance report for the old device
D. To restore settings on the new device after replacement
Answer: D
Explanation:
Backing up the configuration of a network device before replacement is a critical step to ensure business continuity and minimize downtime. The primary purpose of this backup is to restore the existing settings onto the new device, ensuring that it operates identically to the one being replaced. This process includes preserving interface configurations, routing protocols, access control lists, and other essential parameters. By restoring the backed-up configuration to the new device, network administrators can quickly reintegrate it into the network infrastructure without the need for manual reconfiguration, thereby reducing the risk of errors and service disruptions.
Options A, B, and C do not align with the primary objective of configuration backups in the context of device replacement.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Maintenance and RMA Procedures
Question: 22
DRAG DROP
[Device Configuration and Verification]
Drag and drop the steps from the left into order to capture the status of a Cisco device.
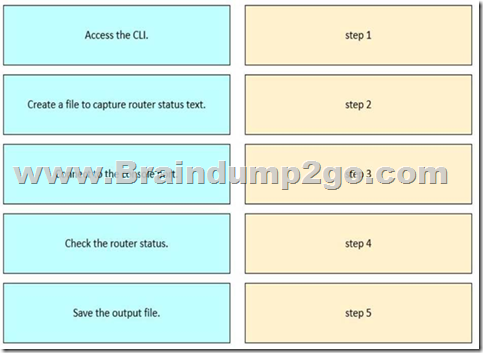
Answer:
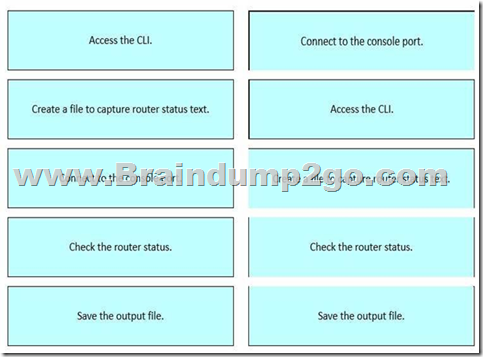
Explanation:
This procedure is taught in the FLDTEC course under the Device Configuration and Verification section and reflects standard field technician workflows:
Connect to the console port using a console cable and terminal software (like PuTTY or Tera Term). Access the CLI of the Cisco device by logging in via the console session.
Create a log file or enable logging in the terminal emulator to begin capturing output.
Check the router status using commands such as show running-config, show ip interface brief, or show version.
Save the output file from the terminal emulator for documentation, troubleshooting, or escalation. This logical flow ensures accurate diagnostics and traceability during field support operations.
Question: 23
DRAG DROP
[Device Configuration and Verification]

Refer to the exhibit. Drag and drop the command names from the left onto the corresponding elements in the interface configuration mode command structure on the right.
Answer:
Explanation:
Component to configure → interface Interface type → FastEthernet
Port → 1 Slot → 0
This command structure is part of the Device Configuration and Verification section in the FLDTEC course. It teaches how to navigate and configure interfaces on Cisco devices using the IOS CLI: interface is the global configuration mode command to begin configuring a network interface.
FastEthernet specifies the type of interface (could also be GigabitEthernet, Serial, etc.). 0/1 represents the slot/port structure used on Cisco devices:
The first digit (before the slash) is the slot number.
The second digit (after the slash) is the port number within that slot.
This structure allows Cisco to modularly address interfaces, especially in devices with multiple slots or module-based configurations.
Question: 24
DRAG DROP
[Cisco IOS Software Basics]
Drag and drop the TFTP statements from the left onto the corresponding categories on the right.

Answer:
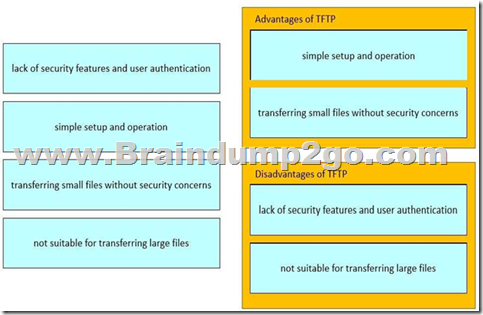
Explanation:
The FLDTEC course teaches that TFTP is a lightweight file transfer protocol often used in Cisco devices for transferring configuration files or IOS images, especially in environments where simplicity is more critical than security:
Advantages:
It has a lightweight footprint, making it easy to use and configure.
Useful for transferring small files such as backup configs or small IOS images. Disadvantages:
Lacks encryption and does not support authentication, making it insecure for sensitive or production environments.
Not efficient for large file transfers due to its limited feature set and reliance on UDP (User Datagram Protocol).
This makes TFTP a good fit for trusted internal networks where simplicity is preferred over robust security.
Question: 25
[Device Configuration and Verification]
Which two settings are standard Cisco console connections when configuring a terminal emulator to connect to the console port of a Cisco switch? (Choose two.)
A. Stop bits: 2
B. Flow control: Hardware
C. Speed (baud rate): 9600
D. Data bits: 8
E. Parity: Even
Answer: C, D
Explanation:
When configuring a terminal emulator (such as PuTTY, Tera Term, or HyperTerminal) to connect to the console port of a Cisco switch, the standard settings are as follows:
Speed (baud rate): 9600
This is the default transmission speed for Cisco console ports, ensuring compatibility across various devices.
Data bits: 8
This setting specifies that each character transmitted consists of 8 data bits, which is standard for most serial communications.
Parity: None
No parity bit is used, meaning there is no additional error-checking bit appended to each character.Wikipedia
Stop bits: 1
One stop bit indicates the end of a character transmission. Flow control: None
No flow control is employed, allowing continuous data transmission without hardware or software- based pausing.
Therefore, options C (Speed: 9600) and D (Data bits: 8) are correct. Options A (Stop bits: 2), B (Flow control: Hardware), and E (Parity: Even) deviate from the standard settings and may result in communication issues if configured.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Device Configuration and Verification
Question: 26
DRAG DROP
[Cisco Equipment and Related Hardware]
Drag and drop the steps of the boot sequence process of a Cisco device into order on the right.
Answer:
Explanation:
Step 1 → Performs power-on self-test (POST)
Step 2 → Loads and runs bootstrap code (firmware) Step 3 → Finds and loads the Cisco IOS software Step 4 → Finds and loads the configuration
Step 5 → Runs the configured Cisco IOS software
This startup process is thoroughly described in the FLDTEC course and aligns with Cisco’s standard IOS boot process:
POST (Power-On Self-Test): Verifies hardware functionality including memory and interfaces. This occurs immediately upon powering the device.
Bootstrap Code Execution: Bootstrap is a small program in ROM that initiates the boot process. Cisco IOS Loading: Bootstrap locates and loads the IOS from flash memory or another source (e.g., TFTP).
Configuration Loading: The router then loads the startup-config from NVRAM (if available).
IOS Execution: Once the configuration is loaded, the device enters operational mode and executes the IOS with the loaded config.
This sequence is vital for field technicians to understand for troubleshooting boot failures or performing device recoveries.
Question: 27
[Troubleshooting Methodologies]
What is the primary purpose of changing the configuration register when performing password recovery?
A. To erase the entire configuration
B. To ignore the startup configuration
C. To unlock all user accounts
D. To enable advanced debugging features
Answer: B
Explanation:
During password recovery on Cisco devices, the configuration register is modified to instruct the device to bypass the startup configuration stored in NVRAM. This allows administrators to access the device without being prompted for existing passwords. The standard procedure involves changing the configuration register value to 0x2142, which tells the device to ignore the startup configuration during the next boot. Once access is gained, the administrator can reset passwords and then restore the original configuration by resetting the configuration register to its default value, typically 0x2102. Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Troubleshooting Methodologies
Question: 28
[Troubleshooting Methodologies]
Which command prompt commands provide the most thorough network diagnostic information when troubleshooting connectivity issues between a Windows PC and a Cisco device?
A.
ipconfig /all ping
B.
netstat -a
netsh wlan show interfaces ipconfig /release
ipconfig /renew C.
ping tracert netstat D.
nslookup arp -a route print
Answer: A
Explanation:
When diagnosing network connectivity issues between a Windows PC and a Cisco device, the combination of ipconfig /all and ping commands provides comprehensive information:
ipconfig /all: Displays detailed IP configuration information, including IP addresses, subnet masks, default gateways, DNS servers, and MAC addresses for all network adapters. This information is crucial for verifying correct network settings.
ping: Tests the reachability of a host on an IP network and measures the round-trip time for messages sent from the originating host to a destination computer. It’s a fundamental tool for checking connectivity between devices.
While other commands like netstat, tracert, nslookup, arp -a, and route print provide valuable information, ipconfig /all and ping are typically the first and most informative commands used in initial troubleshooting steps.
Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Troubleshooting Methodologies
Question: 29
DRAG DROP
[Cisco Equipment and Related Hardware]
Drag and drop the tools from the left onto the corresponding primary functions on the right.
Answer:
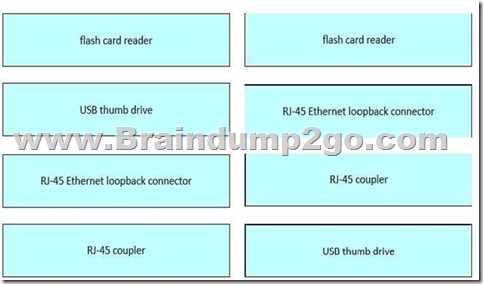
Explanation:
In the FLDTEC curriculum, technicians are trained on physical tools essential for support in the field. These tools and their uses are explained as follows:
Flash Card Reader: Used with removable CompactFlash cards commonly found in older Cisco routers and switches. These cards hold the IOS image or config files.
USB Thumb Drive: Used for transferring IOS files or configs directly to and from Cisco devices that support USB storage. Convenient for portable backups.
RJ-45 Ethernet Loopback Connector: A diagnostic tool that loops the signal back into the port. Helps verify port functionality by simulating a live Ethernet connection.
RJ-45 Coupler: Allows two patch cables to be connected, effectively extending the reach of a cable — useful in setups where a single cable is not long enough.
Question: 30
[Device Configuration and Verification]
Which mode must the console terminal of the device be in before a prewritten configuration is pasted to transfer the configuration from an old device to a new one?
A. Interface configuration mode
B. Global configuration mode
C. Privileged EXEC mode
D. User EXEC mode
Answer: B
Explanation:
To apply a prewritten configuration to a new Cisco device, the console terminal must be in Global Configuration Mode. This mode allows administrators to enter configuration commands that affect the device’s overall operation. To access Global Configuration Mode, one must first enter Privileged EXEC Mode by typing enable, and then enter configure terminal. Once in Global Configuration Mode,
the prewritten configuration can be pasted, and the device will accept the commands accordingly. Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Device Configuration and Verification
Question: 31
[Maintenance and RMA Procedures]
Which command is used to copy the startup configuration of a device to a USB file system when transferring files to a Cisco device?
A. Router# copy startup-config tftp:// [server_ip]/
[destination_file]
B. Router# copy usbflash0: [filename] startup-config
C. Router# copy startup-config usbflash0: [filename]
D. Router# copy running-config usbflash0: [filename]
Answer: C
Explanation:
To back up the startup configuration of a Cisco device to a USB drive, the command copy startup- config usbflash0:
[filename] is used. This command copies the contents of the startup configuration file stored in NVRAM to a specified file on the USB flash drive. This is particularly useful for creating backups before performing upgrades or replacements. Option A: Copies the startup configuration to a TFTP server, not a USB drive.
Option B: Attempts to copy from the USB drive to the startup configuration, which is the reverse of the desired operation.
Option D: Copies the running configuration, not the startup configuration, to the USB drive. Reference: Supporting Cisco Devices for Field Technicians (FLDTEC) – Maintenance and RMA Procedures
More VMware 800-150 Practice Tests download:
1.2024 Latest Braindump2go 800-150 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/2v0-11-25.html
2.2024 Latest Braindump2go 800-150 PDF and 800-150 VCE Dumps Free Share:
https://drive.google.com/drive/folders/14bgugtl73TGBYRqK0xh0xctOQi3fk7eF?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!